Attacking LM/NTLMv1 Challenge/Response Authentication
In Part 1 of the “LM/NTLMv1 Challenge/Response Authentication” series I discussed how both the LANMAN/NTLMv1 protocols operate and the weaknesses that plague these protocols. In this post I will demonstrate how attackers leverage these weaknesses to exploit the LANMAN/NTLMv1 protocols in order to compromise user credentials.
For the remainder of this article I will be focusing on attacking the SMB protocol (Windows file sharing) as this is where LANMAN/NTLMv1 is most commonly used.
Metasploit
In order for a client host to connect to us, we first need to create a listening SMB service that will accept incoming connections. Fortunately, the Metasploit Framework has already provided us with a module to do this :)
1. Fire up Metasploit
2. Load the SMB server module

Now that we have a listening SMB service, all that is needed is for a victim to connect to our machine. By calling “info” on the SMB server module, the module’s description explains “The easiest way to force a SMB authentication attempt is by embedding a UNC path (\\SERVER\SHARE) into a web page or email message.”
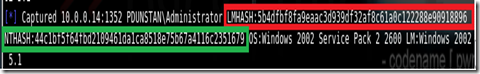
A successful capture will look something like this:

Cain and Abel
The second method we can use to capture a client’s response is by conducting a MITM attack using Cain.
1. Start Cain’s sniffer
2. In the “Sniffer” tab, select the “Plus” icon and choose the hosts victims to poison.

3. Activate Cain’s ARP Poison Routing feature
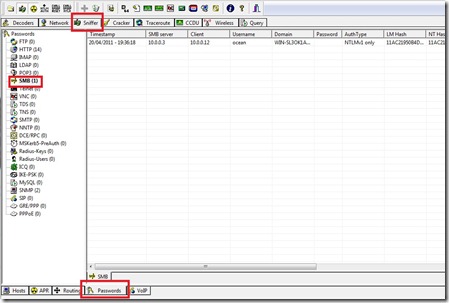
4. Select the bottom “Passwords” tab and wait for the client’s response to appear in the left pane under “SMB”.
Note: It is common practice to use \x11\x22\x33\x44\x55\x66\x77\x88 as the static challenge.
Before we look at each of these methods it should be noted that LANMAN responses are only configured on Windows XP and Server 2003 system (by default). Windows 7, Vista and Server 2008 systems are configured to utilise NTLMv2 by default.
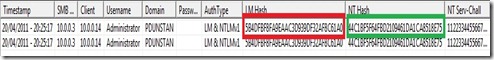
A simple test to check which protocol is currently in use is to see if the LM Hash and NT Hash are different in the capture logs. A difference in these hashes would indicate LANMAN is in in use. If these hashes are the same, LANMAN is disabled and NTMLv1 is in use.
1. Rainbow Tables
As you would remember from Part 1 of this series, the difference between LANMAN challenge/response and NTLMv1 is that the former uses the locally stored LM Hash whilst the latter uses the locally stored NT Hash. This fundamental difference makes a substantial difference when it comes to cracking the LANMAN response. Because LANMAN utilises the weaker LM hashing algorithm, an attacker can trivially obtain the plain-text of a LANMAN response within minutes.
The quickest approach to cracking the LANMAN response is by using rainbow tables. Due to the nature of the LM Hash, rainbow tables are very effective against this hash type. The rainbow tables necessary for this exercise are called “halflmchall” and can be found here. To use these rainbow tables the rcracki_md tool will need to be downloaded.
The following rcracki command will inflate the rainbow table chains and attempt to find the plaintext password for the LANMAN response:
A successful result will look like this:

The remaining characters we can brute force using the Metasploit “halflm_second.rb” script. This can be found in the “tools” directory in the root Metasploit directory. The script is run as follows:
Whilst it is possible to crack an NTLMv1 response using rainbow tables, I have yet to come across any that have been pre-computed. Due to the nature of NT Hashes, NTLMv1 rainbow tables would be far more time consuming to generate and require large amounts of disk space.
2. Dictionary Attack
The second method often used to crack LAMNAM/NTLMv1 responses is a dictionary attack.
I will demonstrate the dictionary attack using two common tools:
The following syntax is used to mount a dictionary attack against LANMAN responses:
To use john against NTLMv1 specify netntlm with the -format flag.
Cain and Abel
If Cain was used to sniff the capture, right click on the entry and select “Send to Cracker”.

In the “Cracker” tab, right click on the entry and choose your appropriate option from the “Dictionary Attack” menu option.

Note: For a list of dictionary files see my post on wordlists.
If you did not capture the response using Cain, and are importing a capture file, the file must be in the following format:
Whilst crude, brute-forcing can be effective against weaker passwords.
To brute-force in Cain, follow the steps detailed above and select “Brute-Force Attack” from the menu item.
For the sake of brevity, I will not go into how John the Ripper can brute-force hashes. This is quite a lengthy topic in itself. Further reading on this topic can be found using Google.
For the remainder of this article I will be focusing on attacking the SMB protocol (Windows file sharing) as this is where LANMAN/NTLMv1 is most commonly used.
Capturing the Response
In order to capture a client’s LANMAN/NTLMv1 response, attackers will often utilise one of two methods:- Force the client host to connect to them
- Conduct a man-in-the-middle (MITM) attack and “sniff” the client’s response
Metasploit
In order for a client host to connect to us, we first need to create a listening SMB service that will accept incoming connections. Fortunately, the Metasploit Framework has already provided us with a module to do this :)
1. Fire up Metasploit
2. Load the SMB server module
msf > use auxiliary/server/capture/smb3. Set the server host address
msf > set srvhost x.x.x.x4. Run the module
msf > run

Now that we have a listening SMB service, all that is needed is for a victim to connect to our machine. By calling “info” on the SMB server module, the module’s description explains “The easiest way to force a SMB authentication attempt is by embedding a UNC path (\\SERVER\SHARE) into a web page or email message.”
A successful capture will look something like this:
Cain and Abel
The second method we can use to capture a client’s response is by conducting a MITM attack using Cain.
1. Start Cain’s sniffer
2. In the “Sniffer” tab, select the “Plus” icon and choose the hosts victims to poison.

3. Activate Cain’s ARP Poison Routing feature
4. Select the bottom “Passwords” tab and wait for the client’s response to appear in the left pane under “SMB”.

Cracking the Response
Three approaches are often referenced when cracking a LANMAN/NTLMv1 response:- Rainbow Tables
- Dictionary Attack
- Brute Force
Note: It is common practice to use \x11\x22\x33\x44\x55\x66\x77\x88 as the static challenge.
Before we look at each of these methods it should be noted that LANMAN responses are only configured on Windows XP and Server 2003 system (by default). Windows 7, Vista and Server 2008 systems are configured to utilise NTLMv2 by default.
A simple test to check which protocol is currently in use is to see if the LM Hash and NT Hash are different in the capture logs. A difference in these hashes would indicate LANMAN is in in use. If these hashes are the same, LANMAN is disabled and NTMLv1 is in use.


1. Rainbow Tables
As you would remember from Part 1 of this series, the difference between LANMAN challenge/response and NTLMv1 is that the former uses the locally stored LM Hash whilst the latter uses the locally stored NT Hash. This fundamental difference makes a substantial difference when it comes to cracking the LANMAN response. Because LANMAN utilises the weaker LM hashing algorithm, an attacker can trivially obtain the plain-text of a LANMAN response within minutes.
The quickest approach to cracking the LANMAN response is by using rainbow tables. Due to the nature of the LM Hash, rainbow tables are very effective against this hash type. The rainbow tables necessary for this exercise are called “halflmchall” and can be found here. To use these rainbow tables the rcracki_md tool will need to be downloaded.
The following rcracki command will inflate the rainbow table chains and attempt to find the plaintext password for the LANMAN response:
> rcracki_mt.exe –h b4dfbf8fa9eaac3 "C:\rainbowtables\*.rti”Note: We are only cracking the first 8 bytes of the captured LANMAN response. Due to the nature of the LM Hash, we are only able to use rainbow tables on the first portion of the LANMAN response. The rest we will have to use brute-force.
A successful result will look like this:

The remaining characters we can brute force using the Metasploit “halflm_second.rb” script. This can be found in the “tools” directory in the root Metasploit directory. The script is run as follows:
# ruby halflm_second.rb –n 5b4dfbf8fa9eaac3d939df32af8c61a0c122288e90918896 –p ADMINISWhere –n is the LANMAN response and –p is the discovered plaintext.
Whilst it is possible to crack an NTLMv1 response using rainbow tables, I have yet to come across any that have been pre-computed. Due to the nature of NT Hashes, NTLMv1 rainbow tables would be far more time consuming to generate and require large amounts of disk space.
2. Dictionary Attack
The second method often used to crack LAMNAM/NTLMv1 responses is a dictionary attack.
I will demonstrate the dictionary attack using two common tools:
- John the Ripper
- Cain and Abel
The following syntax is used to mount a dictionary attack against LANMAN responses:
# ./john –format:netlm /tmp/capture.txtWhere capture.txt is the file containing the LANMAN response. The format of capture file must be as follows:
test::home:5b4dfbf8fa9eaac3d939df32af8c61a0c122288e90918896:44c1bf5f64fbd2109461da1ca8518e75b67a4116c2351679:1122334455667788Where test is the username, home is the workgroup/domain, the first hash is the LM Hash, the second hash is the NT Hash and the final value is the challenge.
To use john against NTLMv1 specify netntlm with the -format flag.
Cain and Abel
If Cain was used to sniff the capture, right click on the entry and select “Send to Cracker”.

In the “Cracker” tab, right click on the entry and choose your appropriate option from the “Dictionary Attack” menu option.

Note: For a list of dictionary files see my post on wordlists.
If you did not capture the response using Cain, and are importing a capture file, the file must be in the following format:
user:workgroup-or-domain:challenge:LMHash:NTHash3. Brute Force
Whilst crude, brute-forcing can be effective against weaker passwords.
To brute-force in Cain, follow the steps detailed above and select “Brute-Force Attack” from the menu item.
For the sake of brevity, I will not go into how John the Ripper can brute-force hashes. This is quite a lengthy topic in itself. Further reading on this topic can be found using Google.

Nema nijednog komentara ;-)
ReplyDelete